Pattern-screen hair on Operating system mobile phones are protected, seemingly so much so that they have confused the Government Institution of Research.
The bureau statements in federal records that 'forensics' professionals conducted “multiple attempts” to accessibility the material of a New samsung Display II mobile phone, but never discover the cellphone.
An Operating system system needs the handset’s The search engines e-mail deal with and its associated with code to discover the mobile phone once too many incorrect swipes are made. The bureau is searching for that information via a court-approved guarantee to The search engines in order to discover a alleged San Diego-area prostitution pimp’s cell cellphone. (For information on the pimp investigation, check out Ars Technica‘s tale on the case.)
Locking down a cellphone is even more important these days than ever because cellular mobile phones shop so much private information. What exactly is more, many declares, such as Florida, allow government bodies the right to accessibility a suspect’s cell cellphone, without a guarantee, upon police detain for any criminal offense.
Forensic professionals and organizations in the phone-cracking space decided that the Operating system passcode hair can beat unwanted uses.
“It’s not irrational they never have the functionality to avoid that on a stay system,” said Dan Rosenberg, a advisor at Boston-based Exclusive Protection Research.
A San Paul federal assess days ago accepted the guarantee upon a ask for by FBI Unique Broker
In a court filing, Cupina wrote: (.pdf)
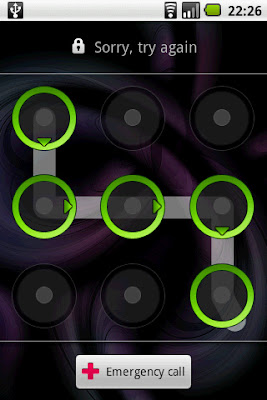
Failure to gain access to the cellular telephone’s memory was caused by an electronic ‘pattern lock’ programmed into the cellular telephone. A pattern lock is a modern type of password installed on electronic devices, typically cellular telephones. To unlock the device, a user must move a finger or stylus over the keypad touch screen in a precise pattern so as to trigger the previously coded un-locking mechanism. Entering repeated incorrect patterns will cause a lock-out, requiring a Google e-mail login and password to override. Without the Google e-mail login and password, the cellular telephone’s memory can not be accessed. Obtaining this information from Google, per the issuance of this search warrant, will allow law enforcement to gain access to the contents of the memory of the cellular telephone in question.
Rosenberg, in a phone appointment, recommended the government bodies could “dismantle a cellphone and draw out information from the actual elements within for anyone looking to get accessibility.”
However, that operates the chance of destructive the cell phone's innards, and avoiding any restoration.
Linda Davis, a speaker for forensics-solutions company Logicube of suv Los Angeles, said police officers is a client of its CellXtract technological innovation, which it promotes as a means to “fast and thorough forensic information removal from cellular mobile phones.”
But that software, she said in a phone appointment, “is not going to work” on a fixed system.
All of which is another way of saying those Operating system display hair are a lot more highly effective than one might suppose.
It was not instantly obvious whether the iPhone’s securing system is as highly effective as its Operating system version. But the iPhone’s passcode has been overcome with simple hackers, the newest of which was unveiled in August 2010.
Clearly, the bureau is none too satisfied about having to call in The search engines for help. The guarantee needs The search engines to convert over Samsung’s “default code” in “verbal” or “written guidelines for overriding the ‘pattern lock’ set up on the New samsung style SGH-T679.”
Google spokesperson Bob Gaither would not say if The search engines would obstacle any element of the guarantee. The search engines, he said, does not thoughts on “specific situations.”
“Like all law-abiding organizations, we adhere to legitimate lawful process. Whenever we obtain a ask for we make sure it satisfies both the mail and soul of the law before submission,” he said in an e-mail. “If we believe a ask for is far too wide, we will try to filter it.”
source
source

















0 komentar:
Posting Komentar